Threat Watch
Threat Watch provides a comprehensive, instant evaluation of your organization's complete cybersecurity health and ex...
Visit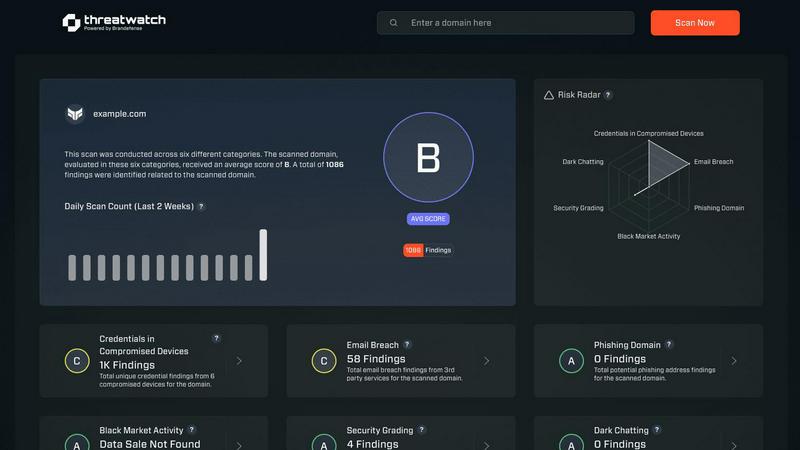
About Threat Watch
In an era defined by digital transformation and escalating cyber threats, organizations of all sizes face the monumental challenge of securing their digital footprint. Threat Watch emerges as a pivotal, unified cybersecurity intelligence solution designed to demystify this complex landscape. It functions as a comprehensive diagnostic and monitoring platform that continuously analyzes an organization's external digital assets, vulnerabilities, and exposures. By aggregating and correlating data from diverse sources, including the dark web, breach databases, and phishing feeds, it delivers a clear, actionable, and real-time picture of an organization's cyber health. The core value proposition of Threat Watch lies in its ability to transform overwhelming threat data into prioritized, understandable insights. It empowers IT security teams, risk management professionals, and business leaders to move from a reactive security posture to a proactive, intelligence-driven strategy. By automating critical assessments and providing continuous visibility, Threat Watch enables organizations to identify lurking threats, prioritize remediation efforts based on actual risk, and mitigate potential damages faster and more efficiently than traditional, manual methods.
Features of Threat Watch
Comprehensive Cyber Health Dashboard
Threat Watch provides a centralized, intuitive dashboard that offers a holistic view of your organization's security posture. This single pane of glass consolidates critical metrics across key security categories, presenting an immediate and clear understanding of your overall cyber health. The dashboard visualizes risk levels, trends over time, and actionable alerts, allowing stakeholders to quickly grasp the current threat landscape without needing to navigate complex, disparate systems.
Real-Time Exposure Detection
The platform continuously scans and monitors a vast array of external sources to detect exposures as they happen. This includes identifying compromised employee credentials circulating on the dark web, detecting corporate assets and devices that have been breached, uncovering phishing addresses impersonating your domain, and monitoring for leaked sensitive company data. This real-time intelligence ensures you are alerted to threats the moment they surface, not weeks or months later.
Automated Asset & Vulnerability Assessment
Threat Watch automates the discovery and assessment of your organization's external-facing digital assets, such as domains, subdomains, and IP addresses. It then proactively scans these assets for known vulnerabilities, misconfigurations, and security gaps. This automated process eliminates manual inventory headaches and provides a continuously updated map of your attack surface, highlighting the most critical weaknesses that require immediate attention.
Prioritized Risk Mitigation Insights
Beyond simple detection, Threat Watch employs intelligent analytics to contextualize and prioritize risks. It correlates discovered vulnerabilities with active threats and exposure data to calculate a realistic risk score for each issue. This allows security teams to focus their efforts and resources on remediating the threats that pose the greatest actual danger to the business, thereby optimizing workflow and improving overall security efficiency.
Use Cases of Threat Watch
Proactive Data Breach Prevention
Organizations use Threat Watch to proactively prevent data breaches by monitoring for stolen employee credentials and corporate data on dark web marketplaces and hacker forums. By receiving immediate alerts when credentials appear, IT teams can force password resets and implement multi-factor authentication before attackers can use the compromised information to gain unauthorized access to corporate networks and cloud applications.
Third-Party and Supply Chain Risk Management
Businesses can extend their security monitoring to assess the cyber health of their critical vendors and partners. By analyzing the external digital footprint of third parties, Threat Watch helps identify if a supplier has suffered a breach or has exposed vulnerabilities that could serve as an entry point into your own systems, enabling more informed vendor risk assessments and contract negotiations.
Executive and Brand Protection
Threat Watch is instrumental in protecting corporate leadership and brand reputation. It detects phishing domains and email addresses that mimic company executives or the official brand, which are commonly used in Business Email Compromise (BEC) and brand impersonation attacks. Early detection allows for swift takedown requests and alerts to employees and customers, mitigating financial and reputational damage.
Compliance and Audit Readiness
For organizations bound by regulatory frameworks like GDPR, HIPAA, or PCI-DSS, maintaining visibility over data exposures is critical. Threat Watch provides continuous evidence of monitoring and due diligence by identifying where company or customer data may have been leaked. This documented oversight supports compliance reports and demonstrates a proactive security stance to auditors and regulators.
Frequently Asked Questions
How does Threat Watch discover my organization's exposed data?
Threat Watch employs a sophisticated, automated engine that continuously crawls and monitors a vast range of sources. This includes public data breaches, paste sites, underground criminal forums on the dark web, peer-to-peer networks, and social media platforms. It uses advanced fingerprinting techniques to associate discovered data—like email addresses, passwords, and documents—with your specific organization's domains and assets.
What is included in the free scan?
The free scan offered by Threat Watch is designed to provide immediate, valuable insight into your surface-level cyber health. It typically includes a high-level assessment across key categories such as the presence of compromised credentials associated with your domain, known breached devices, detected phishing addresses targeting your brand, and any visible mentions of your company's data on dark web sources. It serves as a powerful starting point to understand your exposure.
Do I need to install any software to use Threat Watch?
No, Threat Watch is primarily a cloud-based Software-as-a-Service (SaaS) platform. The initial setup and ongoing monitoring do not require you to install any agents or software on your internal network. You simply register your corporate domains and assets, and the service conducts its intelligence gathering externally. This makes deployment fast, non-intrusive, and scalable.
How is Threat Watch different from traditional antivirus or firewall solutions?
Traditional security tools like antivirus and firewalls are essential defensive controls that operate inside your network perimeter. Threat Watch complements these by operating outside, providing external threat intelligence. It focuses on the threats that haven't breached your defenses yet—like stolen credentials or unpatched public servers—giving you the early warning needed to strengthen your defenses before an attack occurs. It's about prevention rather than just protection.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt is a secure platform that automates contract workflows for fast, compliant, and legally binding e-signatures.
aVenture
aVenture is an AI-powered platform for comprehensive startup research and venture capital intelligence.